Responsible Disclosure and the P4C Bug Bounty
While at Privacy4Cars we don’t routinely do security research, it’s not uncommon for us to discover issues.
We invite researchers who find privacy-related vulnerabilities in vehicles, or who discover vulnerabilities in the wireless stack and wonder how they may apply to vehicles, to contact us and participate in the Privacy4Cars Bug Bounty.
Most importantly, IF YOU SEE SOMETHING, SAY SOMETHING! Millions of consumers’ safety, security, and privacy depends on it.
Some of the issues and vulnerabilities discovered and disclosed by Privacy4Cars include:

CarsBlues Vulnerability Exploit
- A simple to exploit vulnerably that allows access to Call Logs, Text Messages, and More that are stored in the Infotainment Systems.
- CarsBlues uses common, inexpensive devices, off-she shelf free software, and publicly available information to spoof the credentials of past vehicle users
- Tens of millions of vehicles on the road are still vulnerable! CarsBlues works with vehicles across at least 22 vehicle makes and multiple years of manufacturing.
- Disclosed to Auto-ISAC on February 2018.
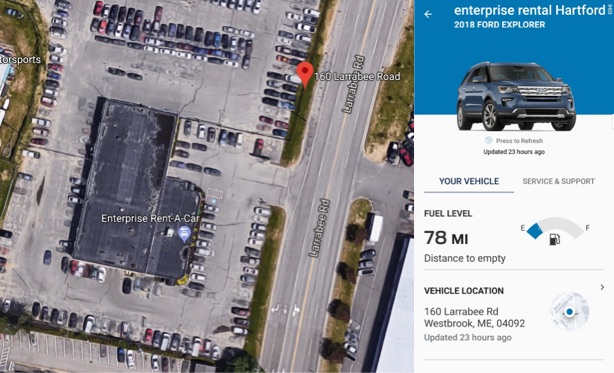
There’s an App for THEFT
- In February 2019 we realized how simple it was to tether a vehicle to which we had access for a few minutes (like a rental or a test drive) to the manufacturer’s app, and from that moment on, follow the vehicle’s every move, and, at any point, locate, unlock, and start the vehicle!
- We tested a variety of connected car apps, and found that in most cases safeguards were low or could be circumvented by a criminal with a combination of social engineering and the image of a fake title
- We responsibly approached manufacturers both directly and through the Auto-ISAC. Most did not respond, or responded that “it is not a hack” and “doing this would be a breach of the Terms of Service” (which will surely keep thieves, fraudsters, and stalkers at bay)
- A year after starting disclosure, ArsTechnica published this article showing consumers had started to discover the issue as well
- We later discovered @RisuToInu (Twitter) had independently discovered and reported the issue to Ford a few months before us. The credit for original discovery should go to her.

Gaming Your Connected Insurance Policy
- We demonstrated that some app-based ”Connected Insurance” can be easily manipulated, pushing driver scores up and insurance rate (fraudulently) down
- Low-Rate Go takes advantage of common and free GPS spoofing apps, which allow to simulate a “perfect driver” (speed just below the limit, no hard braking, etc.) by pre-recording a loop of defined length (e.g. 2 miles) and re-playing it to match the actual odometer read at the end of the day
- We hypothesized it would be possible, in near real time, to harvest from a vehicle the mileage and geolocation, and dynamically create a route that mimics the actual route while maintaining a smooth and below the limit speed.
- Disclosed at the TU Connected Insurance Conference in 2019
CarsBlues Vehicle Hack Exploits Vehicle Infotainment Systems Allowing Access to Call Logs, Text Messages and More
 ATLANTA, GA – NOVEMBER 16, 2018 – Privacy4Cars, the first and only mobile app designed to help erase Personally Identifiable Information (PII) from modern vehicles, publicly disclosed today the existence of a concerning vehicle hack, titled CarsBlues, that exploits infotainment systems of several makes via the Bluetooth protocol. The attack can be performed in a few minutes using inexpensive and readily available hardware and software and does not require significant technical knowledge.
ATLANTA, GA – NOVEMBER 16, 2018 – Privacy4Cars, the first and only mobile app designed to help erase Personally Identifiable Information (PII) from modern vehicles, publicly disclosed today the existence of a concerning vehicle hack, titled CarsBlues, that exploits infotainment systems of several makes via the Bluetooth protocol. The attack can be performed in a few minutes using inexpensive and readily available hardware and software and does not require significant technical knowledge.
As a result of these findings, it is believed that users across the globe who have synced a phone to a modern vehicle may have had their privacy threatened. It is estimated that tens of millions of vehicles in circulation are affected worldwide, with that number continuing to rise into the millions as more vehicles are evaluated.
The hack was discovered by Privacy4Cars founder Andrea Amico during development of the namesake Privacy4Cars app in February 2018. Upon discovery, Amico, a vehicle privacy and cybersecurity advocate, immediately notified the Automotive Information Sharing and Analysis Center (Auto-ISAC), the organization established by the automotive industry to share and analyze intelligence about emerging cybersecurity risks among its members. Amico worked for months with Auto-ISAC to help its affected members understand how an attacker might access stored contacts, call logs, text logs, and in some cases even full text messages without the vehicle’s owner/user being aware – and without the user’s mobile device being connected to the system. Amico recently noticed that at least two manufacturers have made systematic updates to their new 2019 models, making those new models immune to CarsBlues.
“Now that we have completed our ethical disclosure with the Auto-ISAC, we are turning our focus to educating the industry and the public about the risks associated with leaving personal information in vehicle systems,” said Andrea Amico. “The CarsBlues hack, given its ease to replicate, the breadth of situations in which it can be performed against unsuspecting targets, and the difficulty in detecting the exploitation, is a clear indication that industry and consumers alike need to be proactive when it comes to deleting personally identifiable information from vehicle infotainment systems.”
Those most at risk of having their personal information exposed include people who have synced their phones in vehicles that are no longer under their direct oversight, including but not limited to vehicles that have been rented, shared through a fleet or subscription service, loaned, sold, returned at the end of a lease, repossessed, or deemed a total loss. Additionally, people who have synced their phones and given others temporary access to their personal vehicle, such as at dealerships’ service centers, repair shops, peer-to-peer exchanges, and valets may also be at risk for CarsBlues.
Vehicle users should consider deleting personal data from any and all vehicle infotainment systems before allowing anyone access to their vehicle. Industry players should consider instituting a policy to protect consumer data, either by helping customers delete their personal information or by performing the operation themselves – similarly to how telecom carriers handle returned smartphones.
NOTE: At the time of this release Privacy4Cars believes that for the many makes, models, and years affected by CarsBlues, deleting the personal data from the vehicle is the most reliable protection. To fulfill its social mission and commitment to vehicle privacy, Privacy4Cars has decided to continue to offer its namesake app available as a free download for consumers on iOS and Android devices.